
Data streams image generated by the Author using MidJourney
In the era of rapid digital transformation, businesses are constantly evolving to stay competitive and relevant. One of the most significant shifts we’re witnessing is the integration of Information Technology (IT) and Operational Technology (OT), a move that delivers efficiency but also brings new challenges. Cybersecurity challenges are chief among them.
This IT-OT convergence is breaking down the walls of traditionally siloed building networks, seamlessly connecting building operational systems to each other, to IT systems, and to the broader internet, ushering in a new age of interconnected infrastructure.
Understanding IT and OT
In the digital realm, Information Technology (IT) primarily revolves around data-centric systems. These systems encompass computing, storage, and network equipment that form the backbone of our digital world. On the flip side, Operational Technology (OT) is deeply rooted in systems that interact directly with the physical environment. This includes industrial control systems, building management systems, and other technologies that control or monitor tangible processes.
Historically, IT and OT have existed as distinct entities, operating in separate silos. This separation wasn’t just a matter of convention; it was a necessity. Given the unique demands and objectives of each, they developed their own set of protocols, standards, and operational methodologies.
IT and OT in some ways had competing priorities. IT wanted to maximize individual application functionality, data integrity and security while OT wanted to maximize system-wide uptime and data availability for real-time response. To put it simply, IT had to be indestructible and OT had to be uninterruptible.
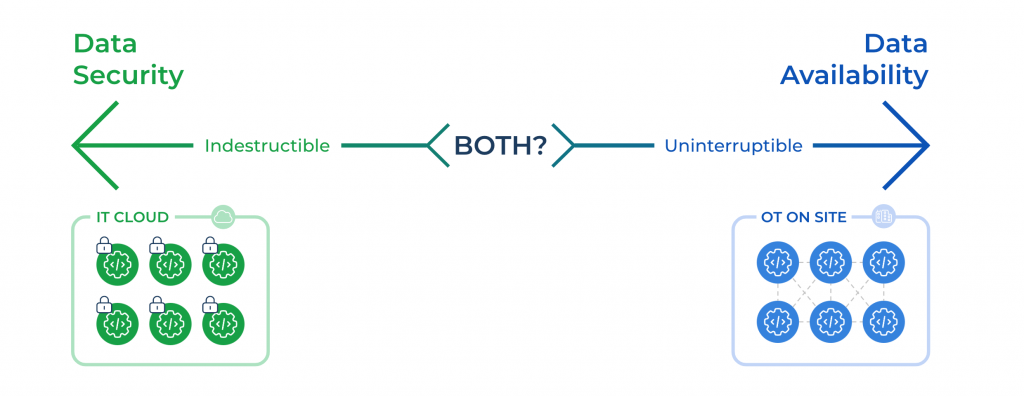
Securely modernizing operational technology (OT) requires the best of IT and OT
The convergence of these two domains was once unthinkable due to their disparate performance needs and the potential risks involved. However, the promise of enhanced efficiency and innovation from combining IT and OT data is driving their integration in today’s interconnected world.
Go deeper on IT – OT differences on pages 28-32 of NIST’s latest Guide to OT Security.
Risks of Cyberattacks in Today’s Landscape
Growing Threat Landscape – The digital age has seen an exponential rise in cyberattacks, with adversaries employing increasingly sophisticated methods to breach defenses. The first half of 2023 has seen a 180% increase in ransomware attacks. Over 40% of cyber attacks exploit OT device vulnerabilities.
Financial Implications – Beyond the immediate financial fallout, a cyberattack can lead to prolonged operational disruptions, resulting in significant revenue loss. The global average cost of a data breach is $4.35 million according to IBM, and over twice that much, $9.4 million, in the U.S.
Reputational Damage – A single breach can erode years of trust, potentially driving away customers and partners.
Regulatory and Compliance Issues – In the wake of an attack, companies may face stringent regulatory penalties, not to mention the legal ramifications of failing to protect customer data. On July 26, 2023, the SEC unveiled new cybersecurity regulations for public companies, real estate trusts (REITs), and private real estate owners operating as vendors to public tenants. The rules require rapid reporting of cyber incidents, ongoing threat monitoring, and transparent risk management.
Amplified Risks with IT and OT Convergence
Expanded Attack Surface – Merging IT and OT environments inadvertently creates more gateways for cyber adversaries, amplifying the potential attack surface. By joining IT and OT networks the vulnerabilities for one become vulnerabilities for the other, multiplying the attack surface. The Target hack where perpetrators used an entry into the HVAC system to move laterally into the point-of-sale systems to get credit card data is a classic example.
Lack of Visibility – Traditional IT security solutions are designed for IT protocols and often fall short in providing comprehensive visibility into OT systems with legacy and bespoke communication protocols, leaving them vulnerable.
Operational Disruptions – A breach in OT systems can have tangible real-world consequences. Imagine the chaos if a city’s utility services were compromised or if manufacturing processes were halted. In the MGM Ransomware attack on September 12, 2023, the attack on an IT system enabled hackers to disable some of MGM’s operational systems including the room key systems such that guests could not get into their own rooms.
Legacy OT Systems – Many OT systems in use today were designed decades ago, long before modern cybersecurity threats and best practices emerged. These systems, often lacking built-in security features, become easy targets.
Single Point of Failure – Centralizing identity solutions like Azure AD for both IT and OT might seem efficient, but it’s a double-edged sword. A compromise in such a system could grant attackers unprecedented access across the board, as seen in the MGM infiltration through the Okta Single Sign-On platform.
Role of Secure Access Service Edge (SASE) in Bridging the Gap
SASE, or Secure Access Service Edge, is a contemporary cybersecurity framework designed to address the unique challenges of the modern digital landscape. There are several benefits of SASE for OT.
Unified Security Posture – SASE offers a harmonized security approach, ensuring both IT and OT are shielded under a single protective umbrella.
Real-time Threat Response – With SASE, organizations benefit from real-time monitoring, ensuring immediate response to any potential threats.
Simplified Management – Managing security across diverse IT and OT environments can be daunting. SASE streamlines this, offering a unified, easy-to-manage solution.
Key Takeaways for CIOs
Proactive Approach – In cybersecurity, a proactive stance is worth its weight in gold. Anticipating threats and preparing in advance can make all the difference.
Continuous Monitoring – The digital landscape is ever-evolving, and so are its threats. Continuous monitoring and timely updates are non-negotiable.
Stakeholder Collaboration – True security is achieved when IT and OT teams come together, sharing insights and collaborating for a holistic security strategy.
As Ben Cooper from BGO insightfully mentioned, “Future-proofing properties to deploy technologies quickly and have better control and management over these technologies not only leads to more efficient buildings but also aligns with company goals for ESG and sustainability.”
This sentiment underscores the importance of adapting and evolving in the face of the digital age.
Key Action
The convergence of IT and OT is inevitable in our quest for digital excellence. However, with this convergence comes amplified risks. It’s imperative for CIOs and technology leaders to recognize these challenges and equip themselves with solutions like SASE to navigate this new terrain confidently.
Don’t expose your IT and OT environments to amplified risk. Reach out to us for a consultation or demo of our Secure Edge SASE product. Let’s work together to fortify your digital landscape.

